Port 443 is the typical HTTPS for all inviolable transactions. It follows that nearly all the secured sites leverage Port 443 for data.
If you are a web developer or a web user, it will help to be conscious of the protection that the secure socket layer certificates (SSL) offer. These certificates are virtual certificates that protect the communications between the server and the client with cryptography.
What’s more? It’s important to assess symbols like the hypertext transfer protocol in the address bar and a bolt in the uniform resource locator (URL).
Once you visit a website without an HTTPs security, your browser will display a caution message “Not secure.” You can guard against the message when you install a secure socket layer certification on your website. How does Port 443 come into play? The hypertext protocol leverages Port 443 to establish a guarded connection.
In this article, we will walk you through all you need to know about HTTPS Port 443.
What is Port 443?
It’s important to know what “port numbers” mean in a computer network before we figure out what Port 443 is. A port number refers to an identity that helps to determine how an internet message has been sent to a web server. For instance, it refers to how HTTP messages always go to Port 443. In addition, port numbers help to identify the senders and receivers of internet messages.
Where can you find port numbers? You will find them at the beginning of the message string.
What’s more? There are numerous types of ports and they all have marked identities like Port 443, Port 80, Port 20, and many others. Internet networks leverage distinct ports to reroute numerous traffics to their endpoints. However, Port 80 is the most commonly used port for all internet servers.
This port is one of the most ideal ports for hypertext protocol services. Hence, you can utilize it for inviolable transactions.
The SSL certificate is worthy of note in the realm of Port 443. It’s because the certification typically establishes an impregnable communication medium between the server and client. The channel encodes all sensitive details and secures them from internet frauds.
Note that the hypertext transfer protocol (HTTP) and hypertext transfer protocol secure (HTTPS) are two distinct internet protocols. In any case, they utilize other ports. The HTTPS typically connect to an internet server over Port 443. But Hypertext Transfer Protocol Secure Port 443 also works well with other hypertext transfer protocol websites. In the same breath, if an HTTPS website fails to operate on Port 443, it may work with Port 80.
What is HTTPS and How it works
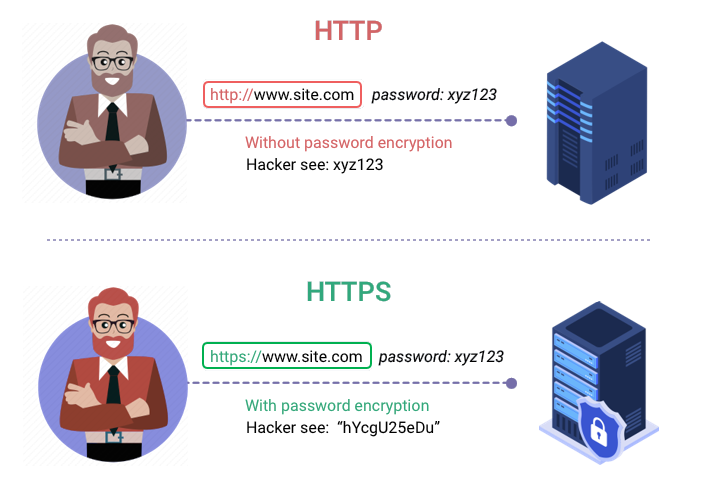
HTTPS (hypertext transfer protocol secure) is the guarded version of HTTP. It’s the primary tool used to reroute data between a computer and a website. HTTPS protects data transfer through encryption. It’s crucial when users transfer guarded data such as email addresses, health insurance details, bank account details, and many others.
Every website that requires sensitive credentials should leverage HTTPS. Innovative browsers like Chrome and Firefox identify websites that do not prominently utilize HTTPS. It will help to look out for a green bolt in the URL icon to find out whether a specific website is secure.
HTTP capitalize on encryption networks to secure internet communications. The network is known as the “Transport Layer Security.” It protects data through what is called the “public key infrastructure.” These security mechanisms use two distinct keys to secure communications between two users.
The public key
it is a significant numerical data used to encode data. You can generate the key through software. But in most cases, reliable authorities provide it. More importantly, it allows everyone to access it through a public server or directory. In other words, any interested individual or company can use a public key.
You can public keys from a certificate authority that issues virtual certificates. These certificates affirm the identity of the owner and comprise the public key.
Note that you will typically find a public key on an asymmetric cryptography infrastructure. It is used to encode data before the internet receives it.
The Private Key
It’s significant numerical data used to encode and decode data. Unlike the public key, only a few individuals or companies can use a private key. In other words, it’s available only to parties authorized to use it. Hence, anyone can send internet data to the private key user but only the user can decode it.
Private keys have longer numerical data, making them secure against severe internet attacks.
Unlike the public key, private keys are faster to use.
What does HTTPS Port 443 secure?
Port 443 protects internet communications between the server and the client with cryptography. It also ensures that your internet access provider (IAP) cannot survey messages or conversations within your server. Hence, this port guarantees your privacy.
One of the trustable symbols is the padlock viewable on the address icon of the site. Although Port 443 signals the website’s security, chances are that a hacker can still tamper with it through security barriers such as data mismanagement.
Hackers can tamper with the following:
- The website you’ve connected.
- The number of website connections.
- Size of the internet messages/ conversations.
- User’s location.
- IP Address.
Hence, it’s crucial to ensure that you do not mismanage your data. HTTPS encode all data and protect them. However, it cannot protect data on a specific network. In this regard, you must send a transmission control protocol (TCP) command through Port 443 to create the hypertext transfer protocol secure connection.
Why is Port 443 Important?
As mentioned earlier, This port is the basic port for all guarded HTTPS traffic. Hence, it’s essential for today’s internet activities. Encoding is vital to secure data, as it interacts with both the server and the client. The encoding mechanism prevents the display of subtle details like banking details on websites with questionable requirements. Any individual can view the conversations between a server and the computer with the standard Port 80, unlike Port 443. That’s one of the reasons Port 443 is essential.
The Port allows websites to utilize both the hypertext transfer protocol and hypertext transfer protocol secure. Most sites are optimized to operate with the combination of Port 443 and HTTPS. But such sites can still work effectively with the combination of Port 80 and HTTPS in special circumstances.
HTTPS used to limit its activities to specific websites. But these days, nearly all browsers shun websites that do not provide the HTTPS service.
How do you use Port 443?
This port doesn’t require anything else before you load it over your server. All you need to get cracking is to insert the string HTTPS:// before clicking the uniform resource locator (URL). But in some cases, it is not essential.
However, you need to access the add-on through the Electronic Frontier Foundation if you must leverage the HTTPS. It will help to explore them on Firefox, Opera, and other browsers indicated on the website.
The computer users need to ensure that they will find their sites via Port 443. It will help to optimize your server to make it available to your website on Port 443.
Note that you need an encryption for your encoding mechanism to work. It will help to purchase a certificate from your service provider or any certificate authorities.
Is HTTPS always leveraging Port 443?
The aim of Port 443 is to manage the HTTPS service. But note that other ports like Port 80 can also manage HTTPS. However, if you want to utilize ports distinct from Port 443, you need to tailor your internet settings to guard against misconfiguration.
However, Port 443 does not guarantee a secure connection. As stated earlier, these ports are simply gateways and exit points to ease communication over the internet server.
Conclusion
It’s an easy enterprise for suspicious characters to read and tamper with one’s details. Although Port 443 has its downsides, it makes the web a secure place.
Numerous certificate providers offer SSL certificates at affordable rates. They manage the website requirements that require protection. In turn, they offer certificates that match the needs of your website.