Proxy servers and VPNs are two of the most useful privacy tools on the internet due to their versatility and effectiveness in hiding your IP address and other identifiable data. Moreover, these tools are helpful for more than one function – they can also allow you access to geo-blocked videos or content. Learn more about how VPN server can useful for fastest connection and robust security.
Let’s discuss the different types of proxy servers and their uses.
Most Common Types of Proxy Servers
A proxy server connects your device with all other servers on the internet. Proxies work by providing you with a new IP address as you use a specific website, app, video game, streaming service, or any other online resource. By using a different IP from your original one, you can access unrestricted content. On top of that, proxies protect you from the dangers of the internet by keeping your IP private.
Different types of proxy servers serve different functions. Some types only support a single function, while others are significantly more versatile. Here are the most common types of proxy servers and their usage scenarios.
HTTP(S) Proxy Servers
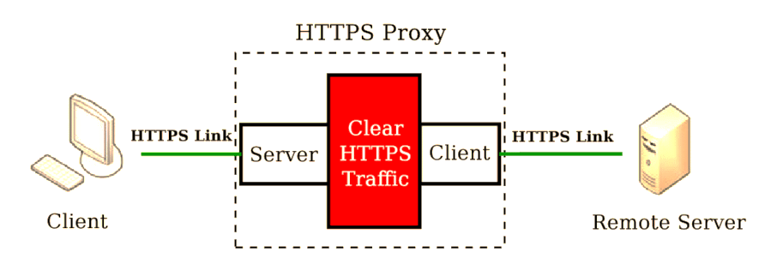
HTTP proxies cater exclusively to web pages. The servers filter the amount of traffic you receive from a web source. The filter is two-way as it also filters users’ information from reaching the web source. The proxy’s IP address is used in all requests instead of the client’s IP.
There are several benefits to using an HTTP proxy:
- They encourage anonymity by allowing users to hide their identity as they surf the web
- They allow tunnel links that provide devices with restricted access to different sites
- They enforce access policies on different sites.
Transparent Proxy Servers
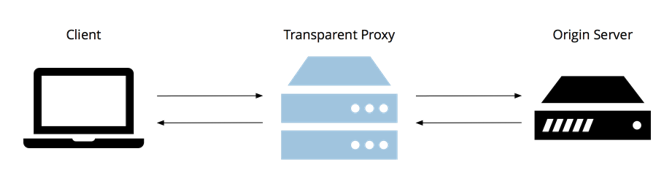
A transparent proxy intercepts the connection between a user and a website. These proxies are transparent because they intercept traffic without modifying requests. Transparent proxies, therefore, exist without an internet user’s knowledge. This type of proxy is popular mostly around monitoring authorities, such as schools, businesses, and institutions. They use proxies to monitor traffic and restrict users from accessing specific websites. Transparent proxies have several other uses, including:
- Filtering out unwanted content
- Modifying or blocking traffic based on specific rules
- Transparent caching of large amounts of data when a website is often accessed by a large number of users.
SOCKS Proxy Servers
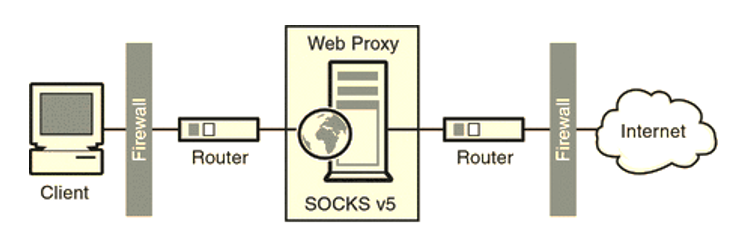
SOCKS proxies are similar to HTTP servers in the way they function. SOCKS are also the most in-demand proxies compared to those listed above, especially due to their versatile support for different communication protocols. The latest SOCKS server is the SOCKS5 proxy server. While they’re more versatile, SOCKS proxies also do not offer standard tunnel encryption like HTTP proxy servers.
SOCKS proxies offer alternative IP addresses for browsing, but they are not limited to web traffic. You can use them for streaming, gaming, online communication and conferencing, and in many other situations where a HTTP(S) proxy can’t work.
ISP Proxy Servers

ISP proxies feature IP addresses from genuine desktop or mobile devices with real ISP-issued internet connections. These can be datacenter proxies or residential proxies. Residential proxies come from genuine desktop and mobile devices. This characteristic makes them the safest type of proxy since it’s impossible for a server to distinguish them from other organic traffic.
While they use ISP IP addresses, datacenter proxies come from online cloud servers, so they’re less “authentic” than residential proxies. However, they usually offer better speeds and unlimited bandwidth at a lower price compared to residential proxies.
Most people are, therefore, more inclined to buy ISP proxies due to the flexibility and added advantages they offer over other types of proxies. Hence, ISP proxies are the most reliable option for situations where privacy is essential, such as:
- Web scraping and gathering data online
- Accessing geo-blocked content
- Accessing limited offers and sales.
Picking A Proxy Provider
Because proxy servers are a measure towards securing your internet, it is essential to research your proxy provider before trusting them with your sensitive data. A reputable proxy provider should offer a no-log policy where they don’t keep any records of your activity or at least a no-share policy where they don’t share or sell this data to third parties. Conducting research on your proxy provider and their policies will help you avoid falling victim to such instances.